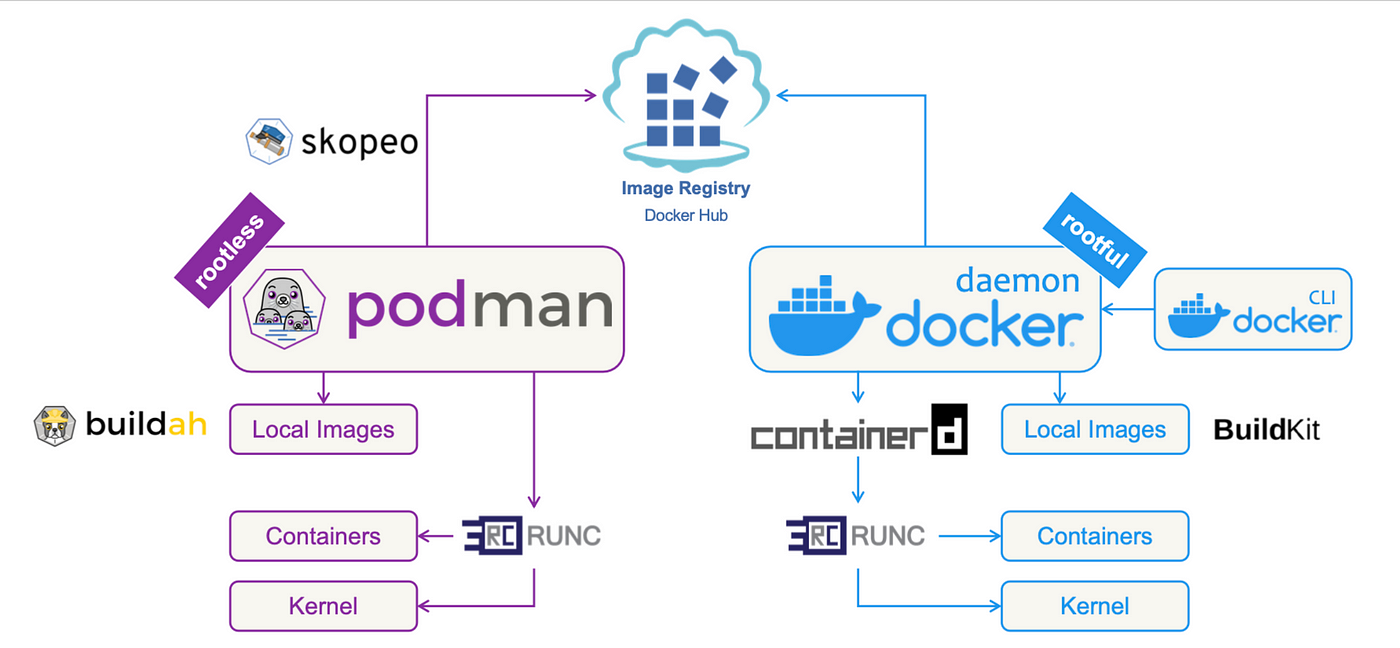
Containers have revolutionized software development and deployment, and two of the most popular container engines today are Docker and Podman. While Docker has long been the industry standard, Podman has gained significant traction—especially in security-conscious and Linux-native environments—thanks to its daemonless, rootless architecture.
In this post, we’ll compare Podman vs Docker across architecture, security, tooling, and ecosystem, and provide practical code examples to help you understand how to use each effectively.
Key Differences Between Podman and Docker
| Feature | Podman | Docker |
|---|---|---|
| Architecture | Daemonless; containers are child processes of the CLI command | Requires a central Docker daemon (dockerd) |
| Rootless Mode | Rootless by default; no special config needed | Rootless available but requires setup; daemon often runs as root |
| CLI Compatibility | Docker-compatible CLI (most commands work with podman alias) | Standard Docker CLI |
| Image Building | Uses Buildah; daemonless, rootless builds supported | Uses Docker daemon with BuildKit backend |
| Pod Support | Supports Kubernetes-style pods natively | No native pod concept; relies on Docker Compose or Kubernetes |
| Systemd Integration | Generates systemd unit files directly for container management | No native systemd integration; requires third-party tooling |
| Security | More secure by design with rootless containers and no daemon | Daemon runs as root by default; larger attack surface |
| Ecosystem | Growing, with Podman Desktop, Podman Compose, and Red Hat support | Mature ecosystem with Docker Desktop, Docker Compose, Swarm |
| Cross-Platform | Linux native, with Windows/macOS support via VM or Podman Desktop | Native support on Linux, Windows, macOS via Docker Desktop |
Why Choose Podman?
- You want rootless, daemonless container management for better security.
- You run containers on multi-user Linux servers and want process-level isolation.
- You want native Kubernetes pod support and easy systemd integration.
- You prefer open-source tooling with modular components (Buildah, Skopeo).
- You want a drop-in Docker CLI replacement without installing a daemon.
Why Choose Docker?
- You want a mature, widely adopted ecosystem with extensive community support.
- You rely on Docker Compose or Docker Swarm for orchestration.
- You want native cross-platform GUI tools like Docker Desktop.
- You need rich third-party integrations and enterprise features.
- You prefer familiar workflows and tooling already established in your team.
Practical Code Examples: Podman vs Docker
1. Run a Simple Nginx Container
Docker:
docker run -d --name nginx-docker -p 8080:80 nginxPodman:
podman run -d --name nginx-podman -p 8080:80 nginxBoth commands run an Nginx container in detached mode, exposing port 80 to host port 8080.
2. Build a Container Image from a Dockerfile
Assuming you have a Dockerfile in your current directory:
Docker:
docker build -t myapp:latest .Podman:
podman build -t myapp:latest .Podman uses the same Dockerfile syntax and can build images rootlessly without a daemon.
3. List Running Containers
Docker:
docker psPodman:
podman ps4. Create and Manage Pods (Podman Only)
Create a pod that shares network and IPC namespaces:
podman pod create --name mypod -p 9090:80Run a container inside the pod:
podman run -dt --pod mypod nginxPodman’s pod concept is similar to Kubernetes pods, grouping containers with shared resources.
5. Generate systemd Unit File for a Container (Podman Only)
Podman can generate systemd service files to manage containers as system services:
podman generate systemd --name nginx-podman --files --newThis creates a .service file you can enable and start with systemctl, simplifying container lifecycle management on Linux servers.
6. Run Containers Rootless (Podman Advantage)
Podman runs containers as your user by default, no root required:
podman run -dt --name rootless-nginx -p 8081:80 nginxDocker requires additional setup for rootless mode and runs a daemon that often needs root privileges.
Performance and Security Considerations
- Podman avoids a central daemon, reducing resource overhead and attack surface.
- Docker’s daemon-based model can consume resources even when idle.
- Both offer near-native container performance.
- Podman’s rootless mode and tighter SELinux integration provide stronger default security.
Conclusion: Which Should You Use in 2025?
| Scenario | Recommended Tool |
|---|---|
| You want ease of use, broad ecosystem, and GUI tools | Docker |
| You prioritize security, rootless operation, and systemd integration | Podman |
| You need Kubernetes pod compatibility and daemonless architecture | Podman |
| You rely heavily on Docker Compose and Swarm orchestration | Docker |
| You want to run containers on multi-user Linux servers securely | Podman |
Both Docker and Podman are excellent container engines fully compliant with OCI standards. Many teams use Docker during development for its ecosystem and switch to Podman in production for its security and flexibility.
Further Reading & Resources
- Podman vs Docker: Key Differences and Which is Better | Last9
- Docker vs Podman: An In-Depth Comparison (2025) | DEV Community
- Podman Official Documentation
- Docker Official Documentation
Optimize your container workflows by choosing the right tool for your environment. Whether you pick Docker or Podman, mastering both will make you a versatile container professional in 2025 and beyond!