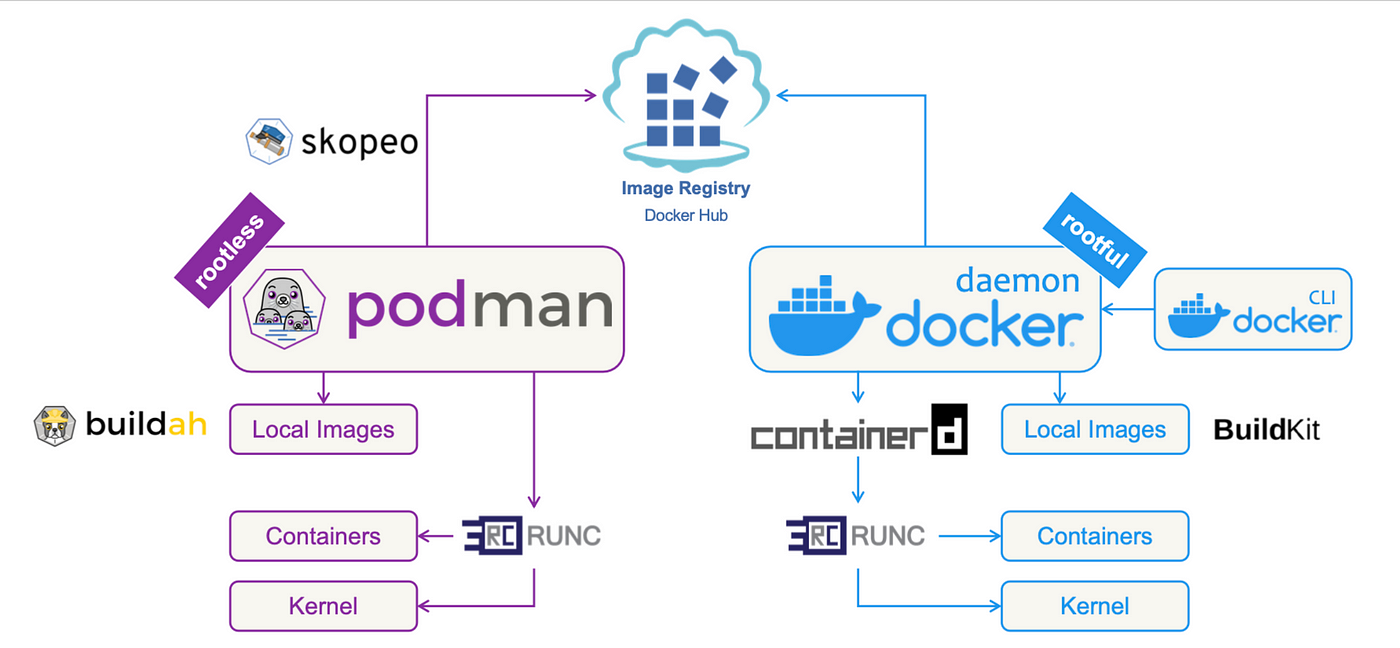
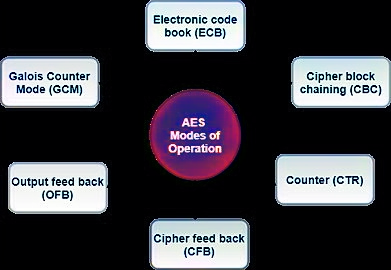
Blog
This blog serves as a knowledge hub for both seasoned professionals and aspiring tech enthusiasts, offering practical insights, technical tutorials, and industry analysis. Join the conversation and stay ahead of the curve.
Articles Explorer
Our newest blog post offers a comprehensive look at software engineering, from foundational concepts to advanced methodologies. Join us as we dissect the intricacies of this dynamic field.
Latest code snippets
Explore a vast library of code snippets, organized by programming language and topic. Find inspiration, learn best practices, and streamline your coding process with our carefully selected examples.
Let's Build Amazing JavaScript Solutions Together
Ready to transform your digital presence with modern JavaScript technologies? I'd love to discuss your web development needs, mobile app projects, or browser extension ideas. Reach out via email at haikel.fazzani@gmail.com. Whether you need React.js applications, Node.js APIs, React Native mobile apps, browser extensions, or full-stack solutions, let's explore how we can bring your vision to life.