“What is ICMP, and why does it matter?” The Internet Control Message Protocol (ICMP) is like the network’s messenger, delivering critical status updates and error reports to keep communication smooth. Whether you’re troubleshooting connectivity or securing a network, understanding ICMP is essential. In this blog post, I’ll break down ICMP in simple terms, provide Linux code examples to demonstrate its use, and include relevant images to make it all crystal clear.
What is ICMP?
ICMP operates at the network layer (Layer 3 in the OSI model) and is a supporting protocol in the Internet Protocol (IP) suite. Unlike TCP or UDP, which handle data transfer, ICMP focuses on diagnostics and error reporting. It’s used by devices like routers and hosts to send messages about network issues, such as unreachable destinations or expired packets. Tools like ping and traceroute rely on ICMP to function.
Think of ICMP as a postal worker who doesn’t carry your letters but tells you if the post office is closed or if your package got lost. It’s not about moving data but about ensuring the network operates efficiently.
Why is ICMP Important?
- Diagnostics: Tools like
pingandtracerouteuse ICMP to check if devices are reachable and measure network latency. - Error Reporting: ICMP informs senders about issues, like a packet being too large or a destination being unreachable.
- Security Considerations: While ICMP is vital, attackers can misuse it for attacks like ping floods or ICMP tunneling, so network admins must manage it carefully.
ICMP Message Structure
An ICMP packet is encapsulated within an IP packet and consists of:
- Type: Defines the message category (e.g., Type 8 for Echo Request, Type 0 for Echo Reply).
- Code: Provides specific details about the message type (e.g., Code 3 for Port Unreachable).
- Checksum: Ensures data integrity.
- Data: Additional information, often including part of the original IP packet that caused the error.
Here’s an image from the web that illustrates the ICMP packet structure:
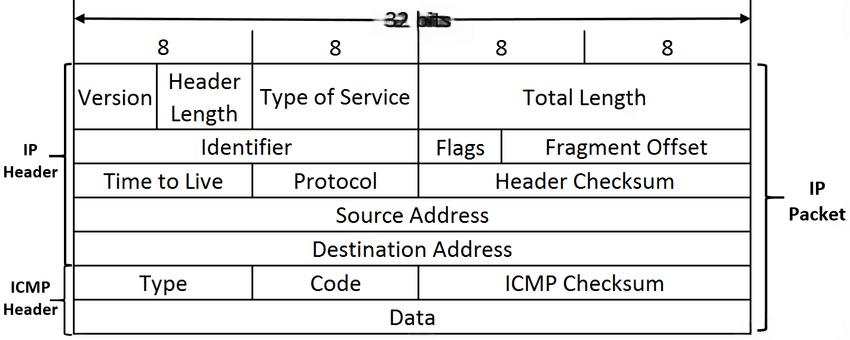 This image shows the ICMP header, including Type, Code, Checksum, and Data fields, encapsulated within an IP packet. It’s a great visual to understand how ICMP messages are formatted.
This image shows the ICMP header, including Type, Code, Checksum, and Data fields, encapsulated within an IP packet. It’s a great visual to understand how ICMP messages are formatted.
Common ICMP Message Types
Here are some key ICMP message types and their purposes:
- Echo Request (Type 8) / Echo Reply (Type 0): Used by
pingto test reachability. - Destination Unreachable (Type 3): Indicates a packet couldn’t reach its destination (e.g., Code 1 for Host Unreachable).
- Time Exceeded (Type 11): Sent when a packet’s Time-to-Live (TTL) reaches zero, used by
traceroute. - Redirect (Type 5): Suggests a better route for packets.
Linux Code Examples
Let’s dive into some practical Linux examples to see ICMP in action. These commands are commonly used by network engineers to troubleshoot and monitor networks.
1. Using ping to Test Connectivity
The ping command sends ICMP Echo Request (Type 8) packets and waits for Echo Reply (Type 0) responses to confirm a device is reachable.
ping -c 4 google.comExplanation:
-c 4: Limits the ping to 4 packets.google.com: The target host.- Output: Shows round-trip time (RTT) and packet loss. If no replies are received, the host might be down, firewalled, or ICMP is blocked.
Sample Output:
PING google.com (142.250.190.78) 56(84) bytes of data.
64 bytes from 142.250.190.78: icmp_seq=1 ttl=117 time=23.4 ms
64 bytes from 142.250.190.78: icmp_seq=2 ttl=117 time=22.9 ms
64 bytes from 142.250.190.78: icmp_seq=3 ttl=117 time=23.1 ms
64 bytes from 142.250.190.78: icmp_seq=4 ttl=117 time=23.0 ms
--- google.com ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms2. Using traceroute to Map Network Paths
The traceroute command uses ICMP Time Exceeded (Type 11) messages to trace the path packets take to a destination.
traceroute -I google.comExplanation:
-I: Forcestracerouteto use ICMP Echo Requests instead of UDP (some systems use UDP by default).- Output: Lists each hop (router) along the path, with latency for each. If you see asterisks (
*), a router might be blocking ICMP.
Sample Output:
traceroute to google.com (142.250.190.78), 30 hops max, 60 byte packets
1 192.168.1.1 1.234 ms 1.456 ms 1.678 ms
2 10.0.0.1 2.345 ms 2.567 ms 2.789 ms
3 * * *
4 142.250.190.78 23.456 ms 23.678 ms 23.890 ms3. Blocking ICMP with iptables
As a security measure, you might want to block certain ICMP messages to prevent attacks like ping floods. Here’s how to block incoming ICMP Echo Requests:
sudo iptables -A INPUT -p icmp --icmp-type echo-request -j DROPExplanation:
-A INPUT: Adds a rule to the INPUT chain (incoming traffic).-p icmp: Specifies the ICMP protocol.--icmp-type echo-request: Targets ICMP Echo Request packets.-j DROP: Drops these packets, preventing the system from responding to pings.
Note: Blocking ICMP can hinder diagnostics, so use this cautiously. For example, blocking all ICMP might break traceroute.
4. Monitoring ICMP Traffic with tcpdump
To capture and analyze ICMP packets, use tcpdump:
sudo tcpdump -i eth0 icmpExplanation:
-i eth0: Specifies the network interface (replaceeth0with your interface).icmp: Filters for ICMP packets.- Output: Shows ICMP packets, including type, code, and source/destination IPs.
Sample Output:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
12:34:56.789123 IP 192.168.1.100 > 142.250.190.78: ICMP echo request, id 12345, seq 1, length 64
12:34:56.812345 IP 142.250.190.78 > 192.168.1.100: ICMP echo reply, id 12345, seq 1, length 64Security Considerations
While ICMP is invaluable, it’s also a target for attacks:
- Ping Flood: Overwhelms a device with ICMP Echo Requests, consuming resources.
- ICMP Tunneling: Hides malicious data in ICMP packets to bypass firewalls.
- Ping of Death: Sends oversized ICMP packets to crash systems (largely mitigated in modern systems).
To secure your network:
- Rate Limit ICMP: Use firewalls to limit ICMP traffic (e.g.,
iptablesrules). - Deep Packet Inspection: Monitor ICMP payloads for suspicious activity.
- Selective Blocking: Allow essential ICMP types (e.g., Echo Reply) while blocking others.
ICMP in IPv6 (ICMPv6)
ICMPv6 is the enhanced version for IPv6 networks. It retains core ICMP functions but adds features like Neighbor Discovery Protocol (NDP) for address resolution. For example, ICMPv6 Type 135 messages handle neighbor solicitation. If you’re working in an IPv6 environment, tools like ping6 and traceroute6 use ICMPv6.
Conclusion
ICMP is a cornerstone of network diagnostics and error reporting, powering tools like ping and traceroute. By understanding its structure, message types, and security implications, you can troubleshoot networks effectively and secure them against misuse. The Linux examples above—ping, traceroute, iptables, and tcpdump—are practical tools every network engineer should master.
Whether you’re a beginner or a seasoned admin, ICMP is your ally in keeping networks running smoothly. Just remember to balance its utility with security to keep your network safe!